Install Chef on Ubuntu 20.04
Traducciones al EspañolEstamos traduciendo nuestros guías y tutoriales al Español. Es posible que usted esté viendo una traducción generada automáticamente. Estamos trabajando con traductores profesionales para verificar las traducciones de nuestro sitio web. Este proyecto es un trabajo en curso.
Chef is a free and open source Infrastructure as Code (IaC) application. It’s a configuration management system that allows administrators to provision and manage infrastructure using automation. A complete Chef workflow includes one or more Chef Workstations, a Chef Server, and a set of nodes. This guide provides some background on how Chef works, and explains how to install and configure Chef on Ubuntu 20.04.
What is Chef?
Chef is a IaC application for automating and streamlining the process of provisioning, configuring, deploying, and managing network nodes. It allows for continuous deployment and an automated environment. Chef can manage many types of components including servers, containers, and networking infrastructure.
Chef operates using a hub-and-spoke architecture, with the master Chef Server at the center. One or more Chef Workstations interact with the Server, which automates the configuration of one or more Chef nodes. Configuration assets move from the workstation to the server and finally to the nodes. Workstations cannot interact with the nodes directly. The Chef infrastructure consists of the following components.
- Chef Workstation: A workstation is a server for creating and testing configuration code. The code is then pushed to the Chef Server. Several workstations can interact with the same server, but each workstation only links to one server. The Chef Workstation documentation contains more information on how to use the workstation.
- Chef Server: The Chef Server is the “command center” for the entire system. It stores and maintains all the configuration files, code, and scripts. A Chef Server includes many components, including a web server and PostgreSQL database. It is responsible for pushing the relevant assets to the various nodes and keeping track of the nodes under its management. Each server is highly capable, efficient, and robust, and is capable of managing a large number of nodes.
- Chef Node: The Chef Server deploys and manages a node using assets developed on the Chef Workstation. Each node is administered by a single Chef Server. Although it is dependent on the server, a Chef Node contains a Chef client. The client queries the server for updates and keeps the node up to date.
The following illustration indicates the relationship between the three parts of the Chef system.
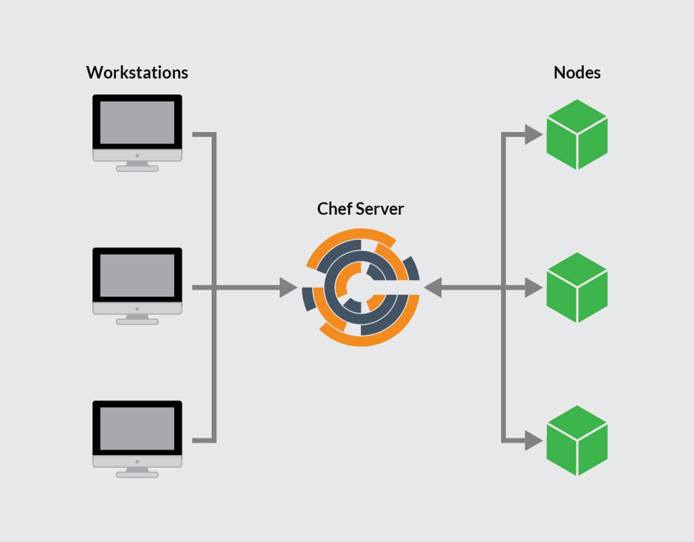
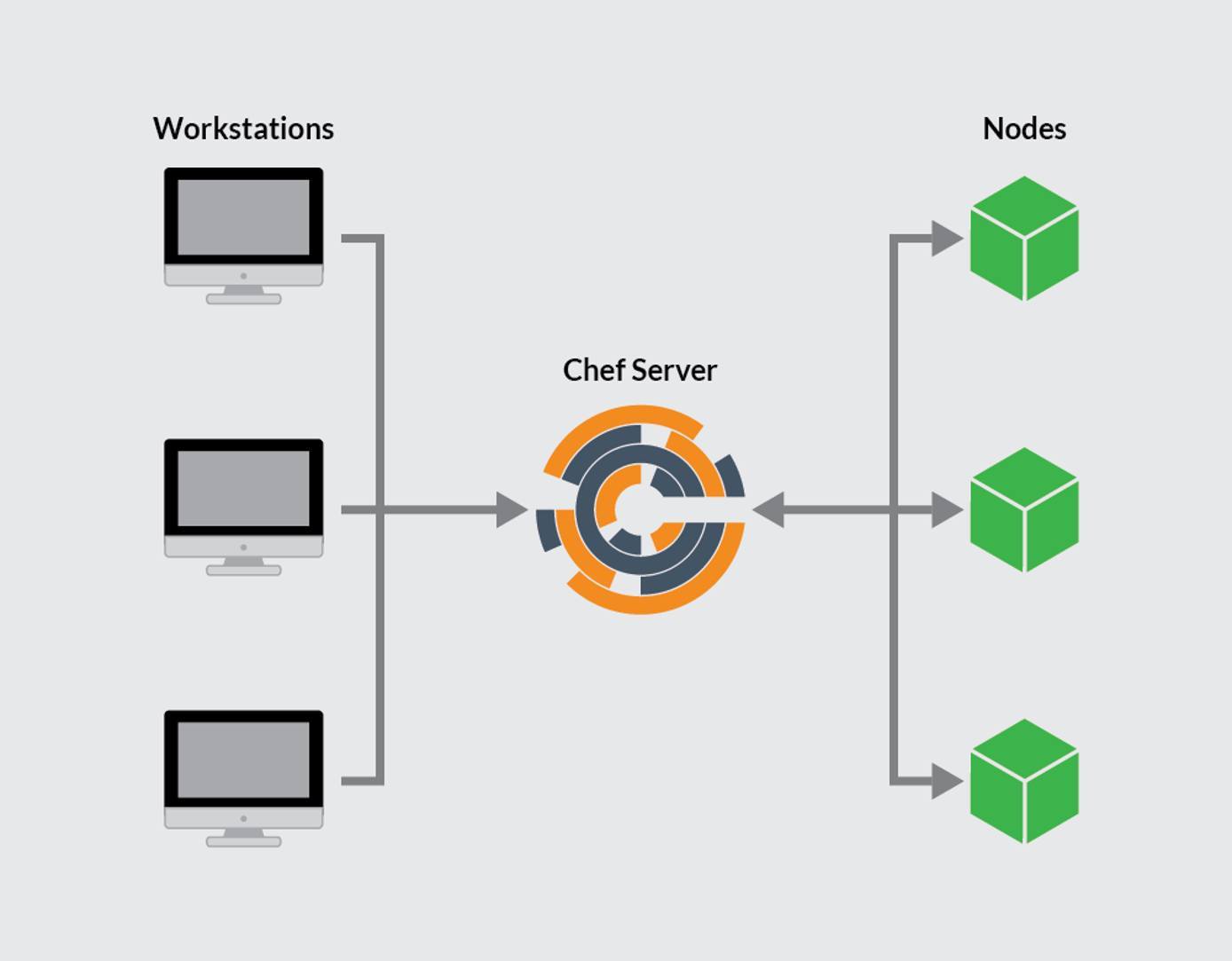
The workstations use Chef commands, such as the knife directive, to interact with the server. Chef incorporates extra security and authentication into all of its operations, using public key encryption. However, the Chef system is complex and has a high learning curve.
Chef uses an idiosyncratic terminology based on cooking vocabulary. Some of the more important terms include the following:
- Attribute: Specifies a value for an item on a node.
- Bookshelf: Stores the various cookbooks and assets on a Chef Server using versioning control.
- Chef-client: Runs on the node, and is responsible for verifying whether the node is up-to-date with the assets stored on the server.
- Chef-repo: A directory on the Chef Workstation that contains the local cookbooks and configuration files.
- Cookbook: The primary method of managing nodes. It contains information describing the final state of a node. The Chef server and node use the cookbook to guide configuration. Cookbooks contain recipes, along with attributes, libraries, templates, and scripts. These cookbooks can be developed on the workstation or downloaded from the Chef Supermarket.
- Environment: Collects nodes into groups to better organize them. Similar configurations and scripts can be applied to the entire group.
- Knife: A Chef Workstation uses the
knifetool to correspond with the Chef Server. Aknifecommand usually takes the formatknife subcommand [ARGUMENT] (options). - Recipe: A recipe is contained within a cookbook. It explains the resources to add, change, or run on the node. Recipes are written in Ruby.
- Resource: A resource is part of a recipe. It contains a type, name, and list of key-value pairs for a component.
- Test Kitchen: This is a workstation module to help users test recipes before deployment.
Linode has a helpful Beginner’s Guide to Chef. For detailed information about Chef, see the Chef documentation. Chef also makes the Learn Chef training resource available.
Before You Begin
If you have not already done so, create a Linode account and Compute Instance. See our Getting Started with Linode and Creating a Compute Instance guides.
Follow our Setting Up and Securing a Compute Instance guide to update your system. You may also wish to set the timezone, configure your hostname, create a limited user account, and harden SSH access.
At least three Linode systems running Ubuntu 20.04 are required to implement a Chef system. One server is for the Chef Workstation, the second for the Chef Server, while a third represents a node under administration. Due to Chef’s memory demands, the Chef Server requires a 8GB Linode. The other two servers can be 2GB Linodes. Both the Chef Server and Chef Workstation should be configured using the previous instructions. Chef is used to set up the target node.
Ensure all Linode servers are updated using the following command.
sudo apt update && sudo apt upgradeAssign a domain name to the Chef Server. For information on domain names and pointing the domain name to a Linode, see the Linode DNS Manager guide.
Configure the host name of the Chef Server so it matches the domain name. This allows SSL certificate allocation to proceed normally. To set the host name of a Ubuntu server, use the command
sudo hostnamectl set-hostname <hostname>, replacing<hostname>with the actual name of your domain.
NoteThis guide is written for a non-root user. Commands that require elevated privileges are prefixed withsudo. If you are not familiar with thesudocommand, see the Users and Groups guide.
How to Install and Configure the Chef Server
Because the Chef Server operates as a hub for the entire system, it is best to install and configure it first. The Chef Server uses a high amount of resources, so it is important to use a dedicated Linode with at least 8GB of memory.
How to Install the Chef Server
The Chef Server Core can be downloaded using wget. The following steps demonstrate how to download the latest release of Chef for the Ubuntu 20.04 release. For other releases of Ubuntu, see the
Chef download page. For more detailed instructions, see the
Chef Server installation page. To install the Chef Server, follow these steps.
Download the Chef Server core using
wget.wget https://packages.chef.io/files/stable/chef-server/15.1.7/ubuntu/20.04/chef-server-core_15.1.7-1_amd64.debInstall the server core.
sudo dpkg -i chef-server-core_*.debSelecting previously unselected package chef-server-core. (Reading database ... 108635 files and directories currently installed.) Preparing to unpack chef-server-core_15.1.7-1_amd64.deb ... Unpacking chef-server-core (15.1.7-1) ... Setting up chef-server-core (15.1.7-1) ... Thank you for installing Chef Infra Server!For better security and to preserve server space, remove the downloaded
.debfile.rm chef-server-core_*.debStart the Chef server. Answer
yeswhen prompted to accept the product licenses.Note
The installation process takes several minutes to complete. Upon a successful installation, the messageChef Infra Server Reconfigured!is displayed.sudo chef-server-ctl reconfigure
How to Configure a Chef User and Organization
To use Chef, configure an organization and at least one user on the Chef Server. This enables server access for workstations and nodes. To create these accounts, follow these steps.
Create a
.chefdirectory to store the keys. This should be a subdirectory located inside the home directory.mkdir .chefUse the
chef-server-ctlcommand to create a user account for the Chef administrator. Additional user accounts can be created later. Replace theUSER_NAME,FIRST_NAME,LAST_NAME,EMAIL, andPASSWORDfields with the relevant information. For the--filenameargument, replaceUSER_NAME.pemwith the user name used earlier in the command.sudo chef-server-ctl user-create USER_NAME FIRST_NAME LAST_NAME EMAIL 'PASSWORD' --filename ~/.chef/USER_NAME.pemReview the user list and confirm the account now exists.
sudo chef-server-ctl user-listUSER_NAMECreate a new organization, also using the
chef-server-ctlcommand. ReplaceORG_NAMEandORG_FULL_NAMEwith the actual name of the organization. TheORG_NAMEfield must be all lower case. The value forUSER_NAMEmust be the same name used in theuser-createcommand. For the--filenameargument, inORG_NAME.pem, replaceORG_NAMEwith the organization name used elsewhere in the command.sudo chef-server-ctl org-create ORG_NAME "ORG_FULL_NAME" --association_user USER_NAME --filename ~/.chef/ORG_NAME.pemList the organizations to confirm the new organization is successfully created.
sudo chef-server-ctl org-listORG_NAME
How to Install and Configure a Chef Workstation
A Chef Workstation is for users to create and test recipes. Any Linode with at least 2GB of memory can be used for this task. Unlike the Chef Server, a workstation can also be used for other tasks. However, in a larger organization hosting many users, it is often efficient to centralize workstation activities on one server hosting multiple accounts.
How to Install a Chef Workstation
The steps for installing a Chef Workstation are similar to those for installing the Server. Download the correct file using wget, then install it. To install a Chef Workstation, follow these steps.
Download the source files for the Chef Workstation. For different releases of the Workstation, or downloads for earlier releases, see the Chef Workstation Downloads page. For more information on the installation process, see the Chef Workstation Installation Documentation.
wget https://packages.chef.io/files/stable/chef-workstation/22.10.1013/ubuntu/20.04/chef-workstation_22.10.1013-1_amd64.debInstall the Chef Workstation.
sudo dpkg -i chef-workstation_*.debThank you for installing Chef Workstation!Remove the source file.
rm chef-workstation_*.debConfirm the correct release of the Chef Workstation is installed.
chef -vChef Workstation version: 22.10.1013 Chef Infra Client version: 17.10.0 Chef InSpec version: 4.56.20 Chef CLI version: 5.6.1 Chef Habitat version: 1.6.521 Test Kitchen version: 3.3.2 Cookstyle version: 7.32.1
How to Configure a Chef Workstation
A few more items must be configured before the Workstation is operational. Tasks include generating a repository, editing the hosts file, and creating a subdirectory. To fully configure the workstation, follow these steps.
Generate the
chef-reporepository. This directory stores the Chef cookbooks and recipes. Enteryeswhen asked whether to accept the product licenses.chef generate repo chef-repoYour new Chef Infra repo is ready! Type `cd chef-repo` to enter it.Edit the
/etc/hostsfile. This file contains mappings between host names and their IP addresses. Add an entry for the Chef Server, containing the name of the server, which is also the domain name, and its IP address. In this example, this is indicated in the line192.0.1.0 example.com. There must also be an entry for the local server. This is the192.0.2.0 chefworkstationline in the example. This entry must contain the local IP address and the hostname of the server hosting the Chef Workstation. The file should resemble the following example.- File: /etc/hosts
1 2 3127.0.0.1 localhost 192.0.1.0 example.com 192.0.2.0 chefworkstation
Create a
.chefsubdirectory. This is where theknifefile is stored, along with files for encryption and security.mkdir ~/chef-repo/.chef cd chef-repo
How to Add RSA Private Keys
RSA private keys enable better security between the Chef Server and associated workstations through the use of encryption. Earlier, RSA private keys were created on the Chef Server. Copying these keys to a workstation allows it to communicate with the server. To enable encryption using RSA private keys, follow these steps.
NoteSSH password authentication must be enabled on the Chef Server to complete the key exchange. If SSH password authentication has been disabled for better security, enable it again before proceeding. After the keys have been retrieved and added to the workstation, SSH password authentication can be disabled again. See the Linode guide to How to Secure Your Server for more information.
On the workstation, generate an RSA key pair. This key can be used to initially access the Chef server to copy over the private encryption files.
ssh-keygen -b 4096Generating public/private rsa key pair. Enter file in which to save the key (/home/username/.ssh/id_rsa):Hit the Enter key to accept the default file names
id_rsaandid_rsa.pub. Ubuntu stores these files in the/home/username/.sshdirectory.Created directory '/home/username/.ssh'. Enter passphrase (empty for no passphrase):Enter a password when prompted, then enter it again. An identifier and public key are saved to the directory.
Your identification has been saved in /home/username/.ssh/id_rsa Your public key has been saved in /home/username/.ssh/id_rsa.pubCopy the new public key from the workstation to the Chef Server. In the following command, use the account name for the Chef Server along with its IP address.
ssh-copy-id username@192.0.1.0Use the
scpcommand to copy the.pemfiles from the Chef Server to the workstation. In the following example, replaceusernamewith the user account for the Chef Server and192.0.1.0with the actual Chef Server IP address.scp username@192.0.1.0:~/.chef/*.pem ~/chef-repo/.chef/Enter passphrase for key '/home/username/.ssh/id_rsa': username.pem 100% 1674 1.7MB/s 00:00 testcompany.pem 100% 1678 4.7MB/s 00:00List the contents of the
.chefsubdirectory to ensure the.pemfiles were successfully copied.ls ~/chef-repo/.chefusername.pem testcompany.pem
How to Configure Git on a Chef Workstation
A version control system helps the Chef Workstation track any changes to the cookbooks and restore earlier versions if necessary. This example uses Git, which is compatible with the Chef system. The following steps explain how to configure Git, initialize a Git repository, add new files, and commit them.
Configure Git using the
git configcommand. Replaceusernameanduser@email.comwith your own values.git config --global user.name username git config --global user.email user@email.comAdd the
.chefdirectory to the.gitignorefile. This ensures system and auto-generated files are not shown in the output ofgit statusand other Git commands.echo ".chef" > ~/chef-repo/.gitignoreEnsure the
chef-repodirectory is the current working directory. Add and commit the existing files usinggit addandgit commit.cd ~/chef-repo git add . git commit -m "initial commit"[master (root-commit) a3208a3] initial commit 13 files changed, 343 insertions(+) create mode 100644 .chef-repo.txt ... create mode 100644 policyfiles/README.mdRun the
git statuscommand to ensure all files have been committed.git statusOn branch master nothing to commit, working tree clean
How to Generate a Chef Cookbook
To generate a new Chef cookbook, use the chef generate command.
chef generate cookbook my_cookbookHow to Configure the Knife Utility
The Chef Knife utility helps a Chef workstation communicate with the server. It provides a method of managing cookbooks, nodes, and the Chef environment. Chef uses the config.rb file in the .chef subdirectory to store the Knife configuration. To configure Knife, follow these steps.
Create a
config.rbfile in the~/chef-repo/.chefdirectory. This example usesvi, but any text editor can be used.cd ~/chef-repo/.chef vi config.rbUse the following
config.rbfile as an example of how to configure Knife. Copy this sample configuration to the file.- File: ~/chef-repo/.chef/config.rb
1 2 3 4 5 6 7 8 9 10 11current_dir = File.dirname(__FILE__) log_level :info log_location STDOUT node_name 'node_name' client_key "USER.pem" validation_client_name 'ORG_NAME-validator' validation_key "ORG_NAME-validator.pem" chef_server_url 'https://example.com/organizations/ORG_NAME' cache_type 'BasicFile' cache_options( :path => "#{ENV['HOME']}/.chef/checksums" ) cookbook_path ["#{current_dir}/../cookbooks"]
Make the following changes:
node_namemust be the name of the user account created when configuring the Chef Server.- For
client_key, replaceUSERwith the user name associated with the.pemfile, followed by.pem. validation_client_namerequires the sameORG_NAMEused when creating the organization followed by-validator.- the
validation_keyfield must contain the name used forORG_NAMEwhen the organization was created, followed by-validator.pem. - For
chef_server_url, changeexample.comto the name of the domain. Follow the domain name with/organizations/and theORG_NAMEused when creating the organization. - Leave the remaining fields unchanged.
Move back to the
chef-repodirectory and fetch the necessary SSL certificates from the server using theknife fetchcommand.Note
The SSL certificates were generated when the Chef server was installed. The certificates are self-signed. This means a certificate authority has not verified them. Before fetching the certificates, log in to the Chef server and ensure the hostname and fully qualified domain name (FQDN) are the same. These values can be confirmed using the commandshostnameandhostname -f.cd .. knife ssl fetchKnife has no means to verify these are the correct certificates. You should verify the authenticity of these certificates after downloading. Adding certificate for example.com in /home/username/chef-repo/.chef/trusted_certs/example.com.crtTo confirm the
config.rbfile is correct, run theknife client listcommand. The relevant validator name should be displayed.knife client listtestcompany-validator
How to Bootstrap a Node
At this point, both the Chef Server and Chef Workstation are configured. They can now be used to bootstrap the node. The bootstrap process installs the chef client on the node and performs validation. The node can then retrieve any necessary updates from the Chef Server. To bootstrap the node, follow these steps.
Log in to the target node, which is the node to be bootstrapped, and edit the
/etc/hostsfile. Add entries for the node, the Chef server domain name, and the workstation. The file should resemble the following example, using the actual names of the Chef Server, workstation, and the target node, along with their IP addresses.- File: /etc/hosts
1 2 3 4127.0.0.1 localhost 192.0.100.0 targetnode 192.0.2.0 chefworkstation 192.0.1.0 example.com
Return to the Linode hosting the Chef Workstation and change the working directory to
~/chef-repo/.chef.cd ~/chef-repo/.chefBootstrap the node using the
knife bootstrapcommand. Specify the IP address of the target node fornode_ip_address. This is the address of the node to bootstrap. In the following example, use the actual user name and password for the account in place ofusernameandpassword. Enter the name of the node in place ofnodename. AnswerYwhen asked “Are you sure you want to continue connecting”.Note
The option to bootstrap using key-pair authentication no longer appears to be supported.knife bootstrap node_ip_address -U username -P password --sudo --use-sudo-password --node-name nodenameConfirm the node has been successfully bootstrapped. List the client nodes using the
knife client listcommand. All bootstrapped nodes should be listed.knife client listtarget-node testcompany-validatorAdd the bootstrapped node to the workstation
/etc/hostsfile as follows. Replace192.0.100.0 targetnodewith the IP address and name of the bootstrapped node.- File: /etc/hosts
1 2 3 4127.0.0.1 localhost 192.0.1.0 example.com 192.0.2.0 chefworkstation 192.0.100.0 targetnode
How to Download and Apply a Cookbook (Optional)
A cookbook is the most efficient way of keeping target nodes up to date. In addition, a cookbook can delete the validation.pem file that was created on the node when it was bootstrapped. It is important to delete this file for security reasons.
It is not mandatory to download or create cookbooks to use Chef. But this section provides a brief example of how to download a cookbook and apply it to a node.
On the Chef workstation, change to the
~/chef-repo/.chefdirectory.cd ~/chef-repo/.chefDownload the
cron-delvalidatecookbook from the Chef Supermarket. For more information on thesupermarketcommand see the Chef supermarket documentation.knife supermarket download cron-delvalidateDownloading cron-delvalidate from Supermarket at version 0.1.3 to /home/username/chef-repo/.chef/cron-delvalidate-0.1.3.tar.gz Cookbook saved: /home/username/chef-repo/.chef/cron-delvalidate-0.1.3.tar.gzIf the cookbook is downloaded as a
.tar.gzfile, use thetarcommand to extract it. Move the extracted directory to thecookbooksdirectory.tar -xf cron-delvalidate-0.1.3.tar.gz cp -r cron-delvalidate ~/chef-repo/cookbooks/Review the cookbook’s
default.rbfile to see the recipe. This recipe is written in Ruby and demonstrates how a typical recipe is structured. It contains a cron job namedclientrun. This job instantiates a new cron job to run thechef-clientcommand on an hourly basis. It also removes the extraneousvalidation.pemfile.- File: ~/chef-repo/cookbooks/cron-delvalidate/recipes/default.rb
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15# # Cookbook Name:: cron-delvalidate # Recipe:: Chef-Client Cron & Delete Validation.pem # # cron "clientrun" do minute '0' hour '*/1' command "/usr/bin/chef-client" action :create end file "/etc/chef/validation.pem" do action :delete end
Add the recipe to the run list for the node. In the following command, replace
nodenamewith the name of the node.knife node run_list add nodename 'recipe[cron-delvalidate::default]'nodename: run_list: recipe[cron-delvalidate::default]Upload the cookbook and its recipes to the Chef Server.
knife cookbook upload cron-delvalidateUploading cron-delvalidate [0.1.3] Uploaded 1 cookbook.Run the
chef-clientcommand on the node using theknife sshutility. This command causes the node to pull the recipes in its run list from the server. It also determines whether there are any updates. The Chef Server transmits the recipes to the target node. When the recipe runs, it deletes the file and installs a cron job to keep the node up to date in the future. In the following command, replacenodenamewith the actual name of the target node. Replaceusernamewith the name of a user account withsudoaccess. Enter the password for the account when prompted to do so.knife ssh 'name:nodename' 'sudo chef-client' -x usernamenodename Chef Infra Client, version 17.10.3 nodename Patents: https://www.chef.io/patents nodename Infra Phase starting nodename Resolving cookbooks for run list: ["cron-delvalidate::default"] nodename Synchronizing cookbooks: nodename - cron-delvalidate (0.1.3) nodename Installing cookbook gem dependencies: nodename Compiling cookbooks... nodename Loading Chef InSpec profile files: nodename Loading Chef InSpec input files: nodename Loading Chef InSpec waiver files: nodename Converging 2 resources nodename Recipe: cron-delvalidate::default nodename * cron[clientrun] action create nodename - add crontab entry for cron[clientrun] nodename * file[/etc/chef/validation.pem] action delete (up to date) nodename nodename Running handlers: nodename Running handlers complete nodename Infra Phase complete, 1/2 resources updated in 03 seconds
Conclusion
Chef is an infrastructure as code (IaC) application for automating the deployment and management of infrastructure nodes. The Chef architecture consists of the Chef Server, which stores all the procedures, and a Chef Workstation, where the infrastructure code is developed. The managed nodes communicate with the server to receive updates. To use Chef, install the Chef Server and Chef Workstation software. Share RSA keys between the server and workstation, and install version control and the Chef Knife utility on the workstation. Bootstrap the target nodes using the knife bootstrap utility. After a node is bootstrapped, it is possible to download cookbooks and recipes using the node’s run list. For more information, see the
Chef documentation.
More Information
You may wish to consult the following resources for additional information on this topic. While these are provided in the hope that they will be useful, please note that we cannot vouch for the accuracy or timeliness of externally hosted materials.
- Chef Website
- Chef Overview
- Chef Workstation documentation
- Learn Chef training courses
- Chef Workstation Downloads for Ubuntu
- Chef Workstation installation instructions
- Chef Server Downloads for Ubuntu
- Chef Server installation instructions
- Chef Supermarket
- Chef Supermarket documentation
- Chef bootstrap documentation
This page was originally published on
